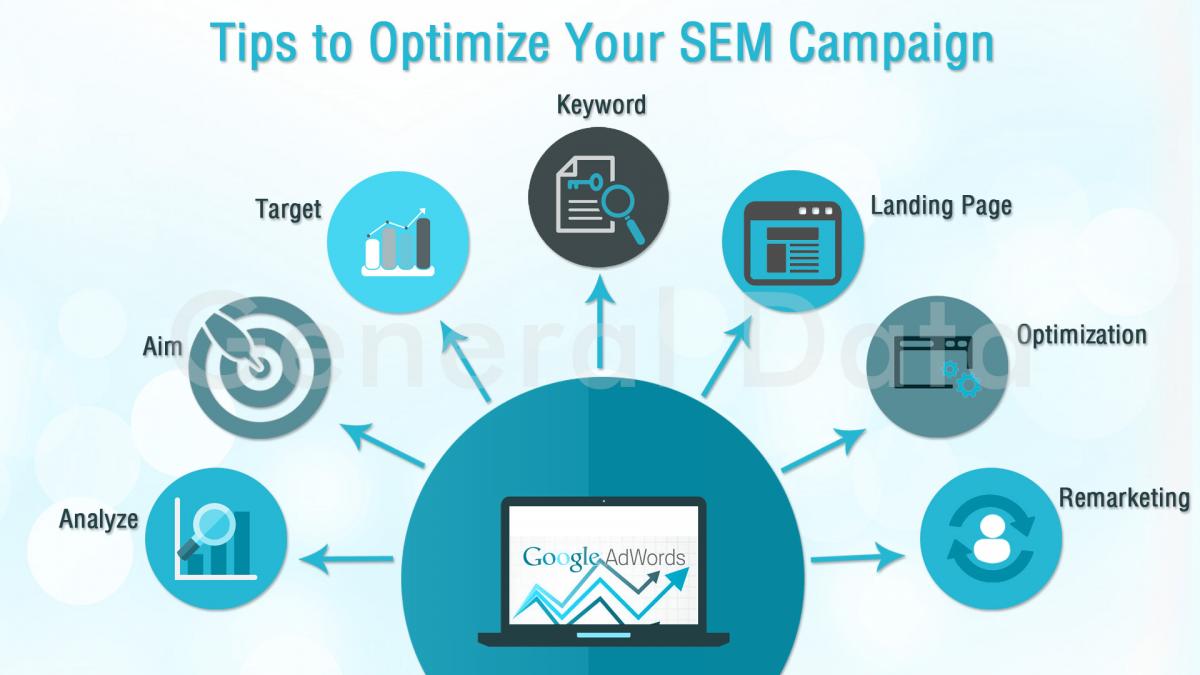
Not All Backlinks are Good for Your Site, So be Careful
Backlinks, or inbound links, are indeed one of the key pillars in constructing an effective SEO strategy. However, navigating the intricacies of backlinks requires careful management. Not all backlinks bring the desired benefits, especially during algorithm changes and the strict …